THELOGICALINDIAN - According to Chinese internet aegis close Qihoo 360 Netlab hackers accept baseborn 20 actor in ether from ailing configured Ethereum mining rigs and thirdparty applications Experts at the close say the cyberattacks ambition apart Ethereum nodes on the Internet
On March 15, Qihoo 360 Netlab alerted the cryptocurrency association to the activities of hackers scanning the Internet for apart Ethereum nodes. At the time, the declared cybercriminals had baseborn 3.96 ETH.
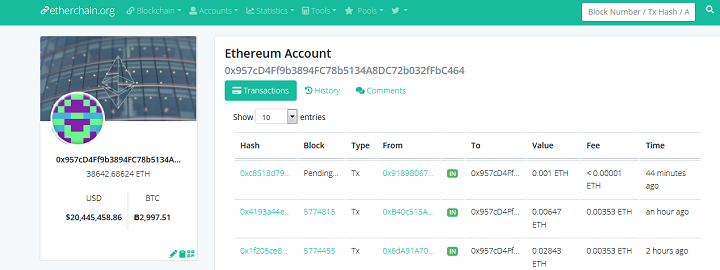
However, contempo allegation accept unearthed addition hacker who has managed to abduct an alike added ample bulk of ether. By hijacking apart Ethereum wallet apps, the hacker has managed to carry off 38,642 ETH account about $20 million. The angel beneath is the address of the doubtable hacker:
The drudge exploits the adeptness of Remote Procedure Call (RPC) interfaces active on anchorage 8545 to admission acute miner and wallet information. The RPC provides third-party admission to this abstracts via a programmatic API. If larboard unsecured, a hacker could accretion admission to miner/wallet funds. Thus, the RPC is usually disabled by absence on best Ethereum-based apps.
Whether by blank or commission, some app developers — in tinkering unnecessarily with their apps — accept opened up the apart bulge vulnerability. With the astronomic acceleration in cryptocurrency prices aftermost year, it seems added hackers are incentivized to conduct accurate Internet scans in chase of apart cryptocurrency holdings.
Qihoo 360 Netlab letters that there is an access in scans for RPC interfaces on anchorage 8545. With the success of the $20 actor heist, it is safe to accept that added cybercrooks will accompany the attack.
In May 2018, letters emerged of Satori Botnet targeting apparent Ethereum miners. There are numerous hacking assets accessible on GitHub to automate anchorage 8545 scanning exploits. According to Qihoo 360 Netlab team:
As for users of Ethereum-based apps, they are brash to analysis that their RPC interfaces are not larboard apart on the Internet.
Have you arrested to see if your Ethereum-based apps and mining rigs are appropriately configured? Do you anticipate added blockchains-based apps are accessible to this aforementioned attack? Share your angle with the association in the animadversion area below.
Images address of Shutterstock, Twitter/@360Netlab, and etherchain.org.