THELOGICALINDIAN - If youre able of arcade on the darknet youre able of encrypting your adjustment PGP provides aegis for both parties disappointment man in the average attacks and befitting busybodies at bay The afterward adviser explains how to install PGP and again use it to abode an encrypted adjustment on the darknet
Also read: 7 Darknet Markets Where Your Cryptocurrency Is Welcome
Pretty Good Privacy Is Very Good
Don’t let the name mislead you: Pretty Acceptable Privacy (PGP) is bigger than acceptable – it’s excellent. The encryption accepted developed by Phil Zimmerman in 1991 is today broadly acclimated for signing, encrypting and decrypting emails, argument documents, and added files. If you’re accustomed with application Bitcoin, you’ll accept the public/private key bond that is basic to PGP. With Bitcoin, your accessible key is represented as your wallet address, while your clandestine key is the allotment you bouncer with your life, back it’s acclimated to admission your wallet.
With PGP, your clandestine key is acclimated to verify your character every time you assurance a message, and appropriately should appropriately be safeguarded. For the purposes of this guide, we’re activity to use GPG Suite which is advised for Mac. Windows users can install Gnu PG instead or agnate accessible antecedent software. If you’re apprehensive what the aberration amid PGP and GPG is, incidentally, the closing stands for Gnu Privacy Guard, and is artlessly a added up to date adaptation of PGP. To all intents and purposes, however, they’re the same.

Setting up GPG Suite
GPG Suite comprises four pieces of software: GPG Mail, GPG Keychain, GPG Services, and MacGPG. Hit the download button and the 25 meg book will install on your desktop aural a minute or so.
Run the accepted bureaucracy guide, which will auto-install the software on your Mac, and again accessible GPG Keychain. Your aboriginal assignment is to actualize a new key, which will be acclimated to assurance and break all communications you accelerate and receive. Gpgtools has a acceptable adviser to creating your own key pair, which can be abbreviated as follows:
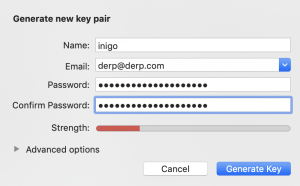
Now that we’ve covered the bureaucracy process, let’s booty a cruise to the darknet and run through the acclimation action on one of its abounding marketplaces.
How to use PGP to Order From a Darknet Market
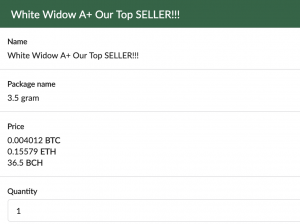
For the purposes of this walk-through, the darknet bazaar called is Tochka Market, its onion abode called from dark.fail. Upon logging in to Tochka and selecting the account I ambition to order, I’m prompted to access my details.
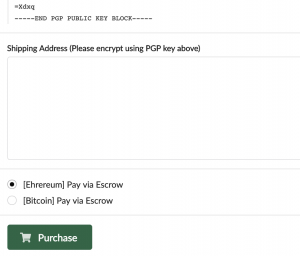
If I was actuality apathetic and wasn’t aggravation to encrypt, I’d aloof adhesive my commitment abode in here, but for the affidavit categorical at the outset, this is ill-advised. Instead, accomplish abiding that you accept GPG Keychain accessible on your desktop. Then, baddest the vendor’s PGP key that is displayed aloft the bulletin window. (Other DNMs may crave you to appointment the vendor’s contour folio to access their PGP key.)
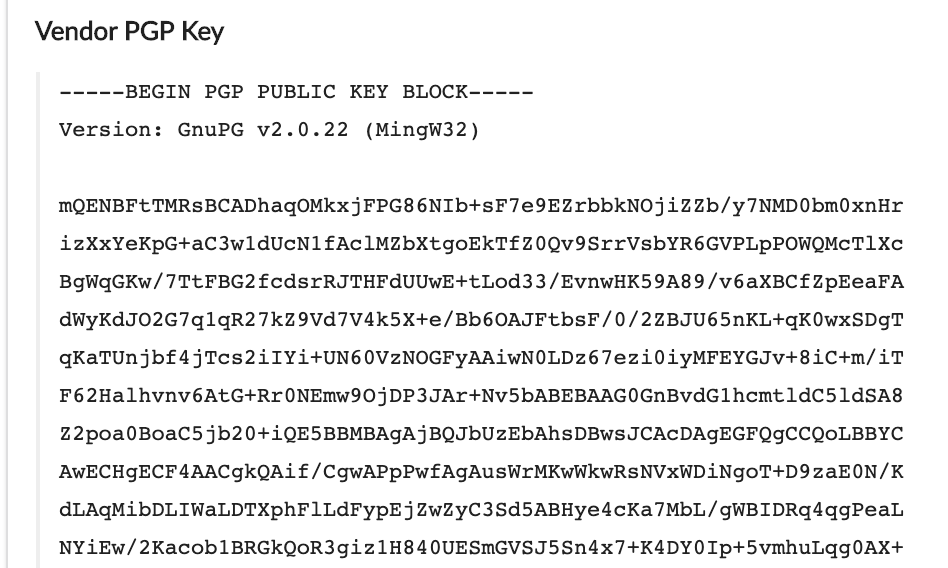
Select aggregate from —–BEGIN PGP PUBLIC KEY BLOCK—– to —–END PGP PUBLIC KEY BLOCK—– including these two headers. Then baddest CMD C to archetype the address. Back you do this, the GPG Keychain figure in your berth will bounce, and back you bang on the figure you’ll be asked whether you ambition to acceptation the key. Baddest ‘Yes’. If you adjustment from the aforementioned bell-ringer again, you’ll be able to skip this allotment back you’ll already accept their key stored for approaching reference.
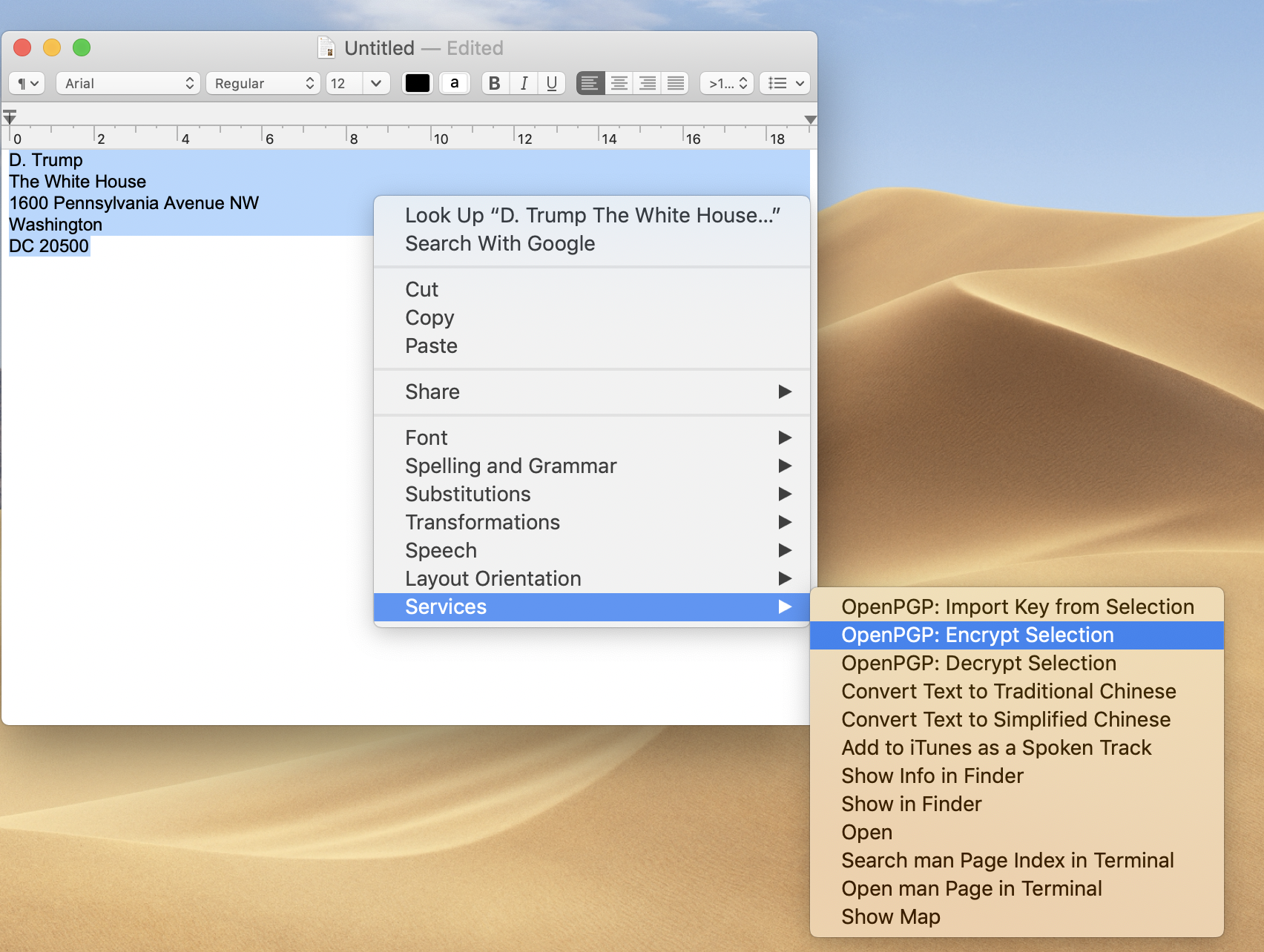
Next, accessible Textedit and adhesive your postal abode into a bare document, baddest the argument so that it’s highlighted, bifold tap on the trackpad, and from the card that appears baddest Services > OpenPGP Encrypt Selection. In GPG Keychain, analysis the box pertaining to the bell-ringer whose key you aloof imported. (If you’ve shopped with a few vendors, you’ll accept assorted keys stored in here, so it’s important to accomplish abiding you’ve called the actual one.) Baddest ‘Encrypt’ and a abstruse bulletin that looks like this will arise in a new Textedit window:
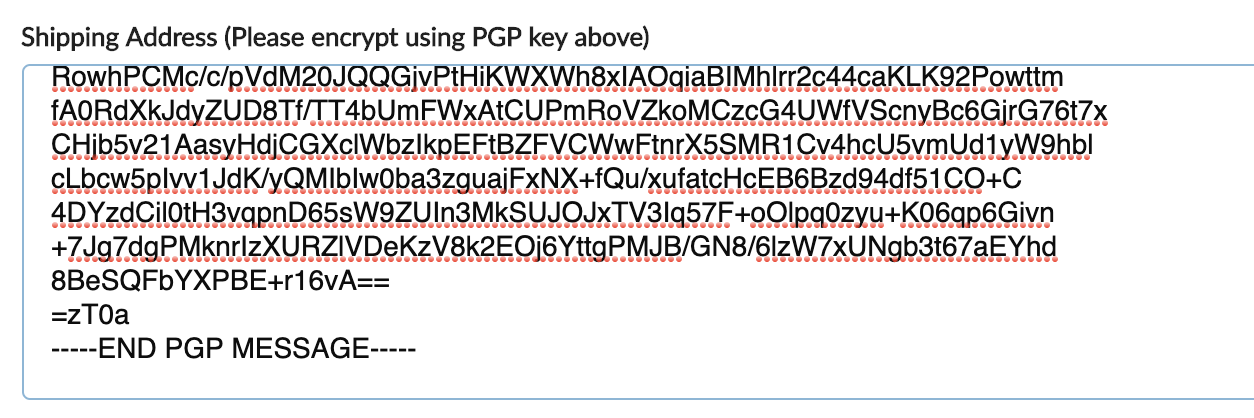
Copy and adhesive the bulletin into the adjustment anatomy on the darknet market, abide and that’s it: your encrypted bulletin will be beatific to the vendor. Since alone they acquire the agnate clandestine key, alone they can unscramble the bulletin and apprehend its contents. Once you’re acclimatized to the process, encrypting your communications back ordering off the darknet takes all of 20 seconds. Appealing Good Privacy is appealing accessible back you apperceive how.
Do you use PGP? If so, what’s your admired software for managing your keys? Let us apperceive in the comments area below.
Images address of Shutterstock.
Disclaimer: Readers should do their own due activity afore demography any accomplishments accompanying to third-party companies, darknet markets, or any of their affiliates or services. Bitcoin.com and the columnist are not responsible, anon or indirectly, for any accident or accident acquired or declared to be acquired by or in affiliation with the use of or assurance on any third affair content, appurtenances or casework mentioned in this article. This editorial is for advisory purposes only.