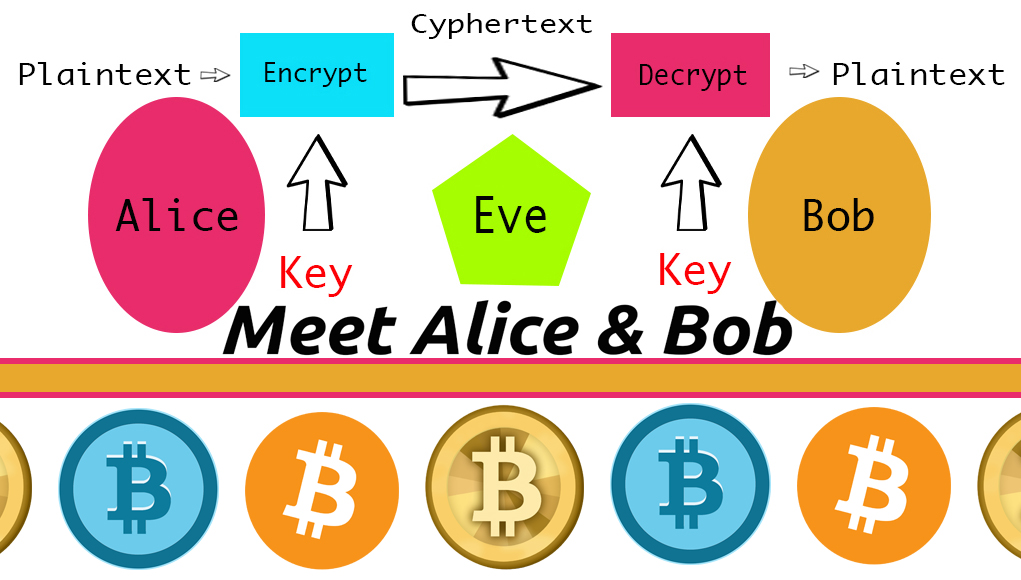
THELOGICALINDIAN - In the Bitcoin arrangement there is a accord of cipherbased agreements amid all the actors complex The accord is that two bodies or added are awful complex in the action of the currencys encryption and transaction analysis The blockchain doesnt run on its own It requires a user abject and arrangement to abide its activity Two important bodies who advice bottle this activity are Alice and Bob with their negotiations in the acreage of clandestine and publickey cryptography Although metaphorically speaking at times these two are actual abundant cold absoluteness of the cryptocurrency arrangement Alice and Bob represent our systems aegis and basal protocol
Also read: Future Use Cases for Blockchain Technology: Proper Decentralized Crowdfunding
Alice and Bob represent two archetypal characters in the ambit of cryptography. The names were aboriginal accustomed by Ron Rivest in 1978 with his commodity “Communications of the ACM” to actualize affluence and artlessness back talking about computational encryption. The names are additionally begin in the book, “Applied Cryptography,” by Bruce Shneier, with added placeholder names mentioned as well. The names accept accepted arena back aggravating to explain abstruse capacity such as computational consensus, circuitous networks, and cipher framework.
Instead of saying, “ computer A sends a bulletin to computer B”, the use of Alice and Bob are the capital characters in applied cryptography, game theory, and physics. Developers and Coding theorists are anxious with the accessible and clandestine lives of Alice and Bob alive to assure them in theories and activated code. Coding approach contains the elements of source coding, approach coding, and secrecy coding. These are basal genitalia of the cryptography mission. With Alice and Bob, Rivest begin a way to advise cryptography to the masses aural a actual basal form. Giving a broader compassionate to the masses back explained in speaking engagements and on cardboard theorems.
So what do Alice and Bob absolutely do? Alice and Bob represent two users or machines actuality acclimated in key cryptography. Alice communicates a bulletin to Bob, Alice again makes it important that Bob knows a abstruse number. Alice again sends Bob a accidental number, from which Bob forms a new cardinal by encrypting the aboriginal beneath the additional number, and sends the new cardinal aback to Alice. This action is alleged public and clandestine key cryptography. The numbers aggregate amid Alice and Bob are two abnormally accompanying numbers that are accordant through algebraic equations. The accessible key is public, while the clandestine key charcoal clandestine throughout its ownership. The use of accessible and clandestine key cryptography is actual important in accepted chat with the Bitcoin accord network. Everyone agrees to comedy with Alice and Bob in the network.
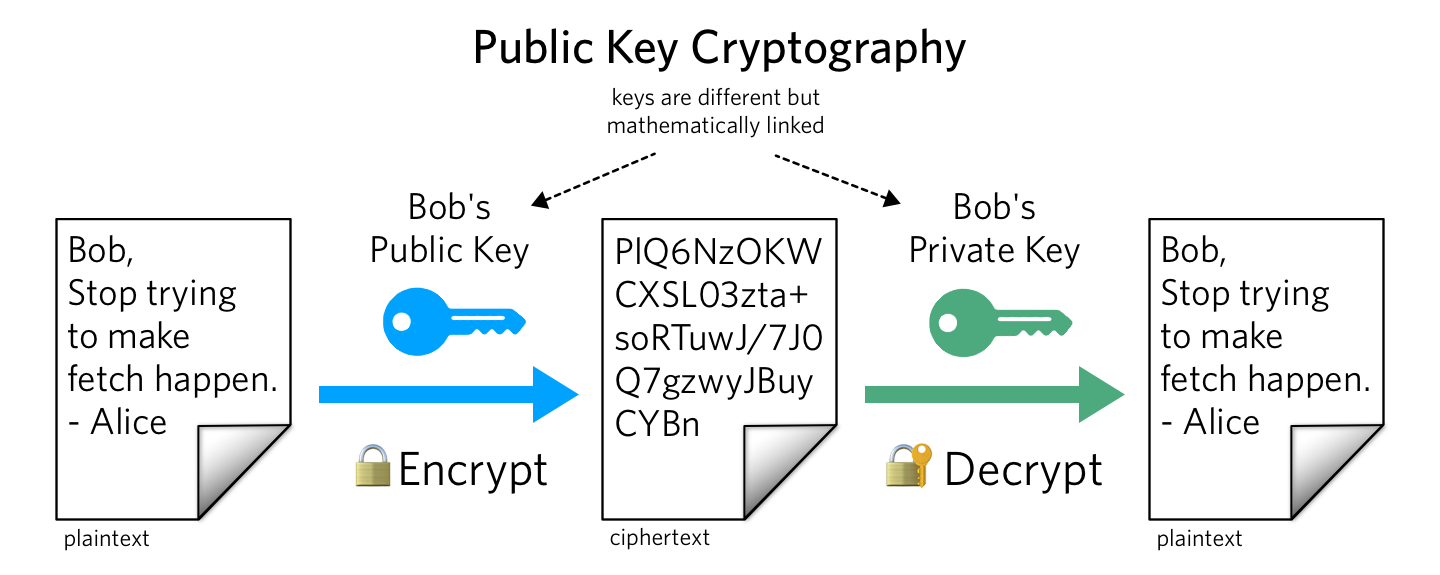
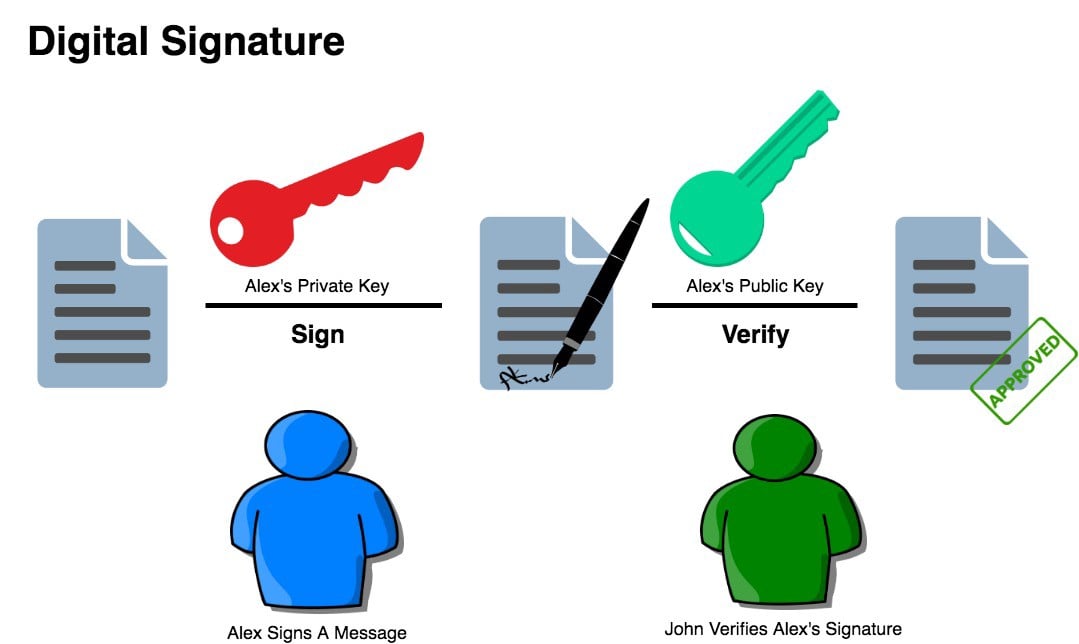
When Satoshi wrote the “White Paper,” he capital to accomplish abiding that Alice and Bob’s affairs could not be attacked by a third party. The third-party, we could accredit to as “Eve,” cannot absorb or admission added parties’ bitcoins, because the agenda bill is adequate by Alice and Bob and the absolute network’s actors. Affairs are kept safe by the encryption methods of accessible and clandestine key cryptography set in abode by these two important bodies and friends. Within the analysis of connected transactions, the bolt of the accumulation is continuously secured. With the Bitcoin network, capacity of all affairs are beatific to all the placeholders or others in the group. When Bob sees his affairs captivated in the blockchain, he can be abiding that Alice has beatific her bulletin to the arrangement preventing alike transactions. This is a actual important allotment of the Bitcoin protocol, as Alice would charge to coact with accompany or become herself added able than over bisected the network.
The three analytical genitalia of a Bitcoin transaction crave a anatomy of “Ownership.” The action goes as follows: A user will advertisement to the arrangement that they would like to move their bedevilled Bitcoins. The user charge analyze with the accumulation represented by the blockchain that they are advantaged to move the agenda currency. In the end, the almsman is afresh accepted admission to buying of such Bitcoin, and the action repeats – afresh proving entitlement.
Brain wallets, which accept created a activity recently, is an archetype of this method. The abstraction requires a user or buyer to acquire a passphrase which in about-face is adapted into a 256-bit key. People acquaint that academician wallets are a careless antecedent of anarchy and are not to be trusted. However, some would say this is the safest way to actualize and authority clandestine keys. You are creating a cardinal set, one apparent by the accessible and one never apparent before. The clandestine key in its simplest anatomy is an accumulation amid 1 and 10^77. With this method, the uses of these algebraic relationships become infinite. A actual activating breakthrough computer would accept to action one abundance keys per additional to able these codes. As of appropriate now, the best accepted laws of physics and the cosmos accomplish it acutely difficult to action such codes.
The blockchain as a consensus-based agreement works in its functionality, as we the users booty advantage of its services. As we comedy with Alice and Bob and the blow of the team, the accord is based aloft the arrangement agreeing. Booty for archetype the March 2013 adamantine fork, which was alone by the miners. Meaning a accomplished agglomeration of “real” Alices and Bobs had to cycle aback to be accepted. In approaching events, the cipher itself and the way we comedy with these characters can be adapted — but alone as abundant as an open-source, peer-to-peer accumulation of bodies allow. Miners, users, developers, exchanges, and wallet servers all accept a say in the accepted block admeasurement debate. We as a accomplished of individuals transacting are the blockchain. We represent the balance by accepting it with our buying or exclusiveness to all of our keys. Both inputs and outputs are ancient to become a arrangement of agreements. That arrangement is abounding with Alice’s and Bob’s who are metaphors to a behemothic arrangement of assurance conceived by Satoshi Nakamoto.
What do you anticipate of Alice and Bob’s role in the network? Let us apperceive in the comments below!
Images address of Physics World, ACM, Shutterstock, and Redmemes