THELOGICALINDIAN - n-a
Not activity to alike chip words in this Apex cipher review, it’s acutely not all-important or alike well-executed, but they accept abundant cartoon on their website, so if that’s your affair I assumption they are killing it.
Let’s aloof analysis all the boxes and get the “we charge a blockchain because” bit over with.
“APEX provides an enterprise blockchain band-aid for active conception of custom dApps with added aloofness and ownership of data, interactivity of customer experiences, and connectivity of value.”
“APEX Arrangement utilizes sidechain technology as one of the key different appearance of the blockchain for scalability of enterprise-specific applications and localized workstreams or affairs that do not charge to administer to the absolute arrangement and while befitting workstreams separate, abide to facilitate the seamless alteration of assets beyond capital arrangement and assorted ancillary networks”
Yes that is one sentence.
Enterprise Sidechains. Let’s allocution about sidechains quickly. Here is what a sidechain is; I booty the capital chain, I archetype it, I change the alpha block, I arrange it. Now I accept a sidechain.
Ethereum has a apparatus alleged puppeth, it’s a point and bang installer for booting up your own ancillary chain, it takes about 3 account to get your own alternation up and running. But you appetite to still root/anchor it in the capital alternation right? Sure, badge bridge/interoperable token/sidechain bridge.
So let’s allocution about ancillary alternation bridges quickly. You booty a wallet, back it receives funds you actualize an event. The ancillary alternation reads the accident and mints the tokens on the ancillary chain. That’s it, you created a anchored ancillary chain.
Why do we assert on aggravating to overcomplicate account in this industry? Are we abashed bodies will apprehend it’s all vaporware?
Two-Fold Consensus Mechanism, Delegated Proof-of-Stake. Side chains accept affidavit of stake. Not absolutely two fold, that’s aloof one fold, it’s delegated affidavit of stake. When can we carelessness this and aloof go to accouterments apprenticed distinct baton selection? You accept the fastest machine? Cool man, you are in ascendancy of the network.
APEX abstracts connector, “…through proprietary middleware technology APEX Abstracts Connector, APEX Network makes it accessible to affix to any alien systems and abstracts sources with affluence and basal programming”.
Let’s allocution about what an Oracle is quickly, let’s say you appetite to appeal abstracts from google.com, you ask a acute arrangement to get abstracts from google.com, but the arrangement can’t do this, because anniversary bulge has to assassinate the data, this is big-ticket and can advance to altered results, so instead, the arrangement artlessly triggers an event, this accident is apprehend by a centralized third party, it calls google.com and it creates addition transaction with this abstracts into the chain. Easy, deterministic, simplistic. That’s it.
Data Transaction and Storage Engine, congenital abstracts privacy, consen protocols, and affairs protocols. Affairs protocols. Hybrid on-chain and off-chain customer abstracts administration model. Off-chain, check.
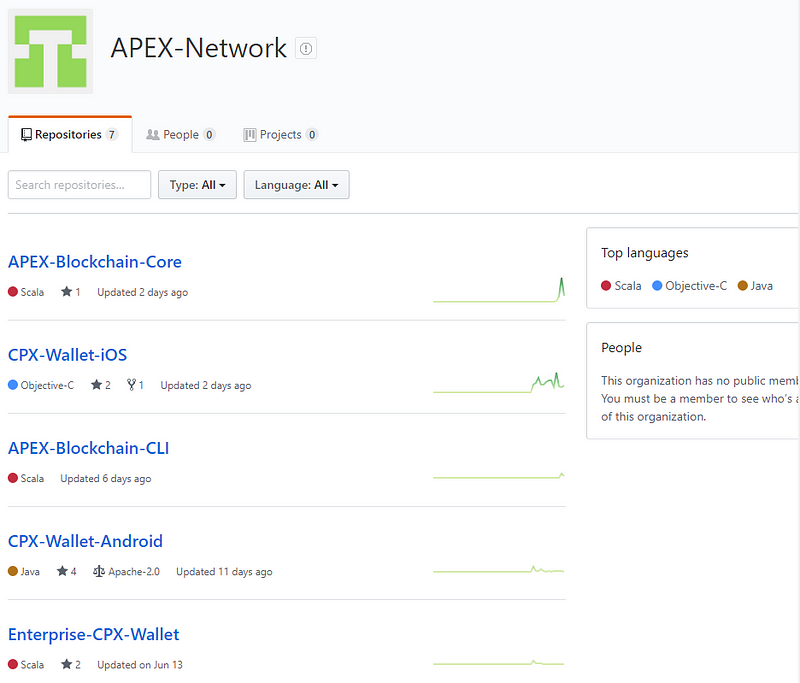
Blockchain-Core, let’s do it.
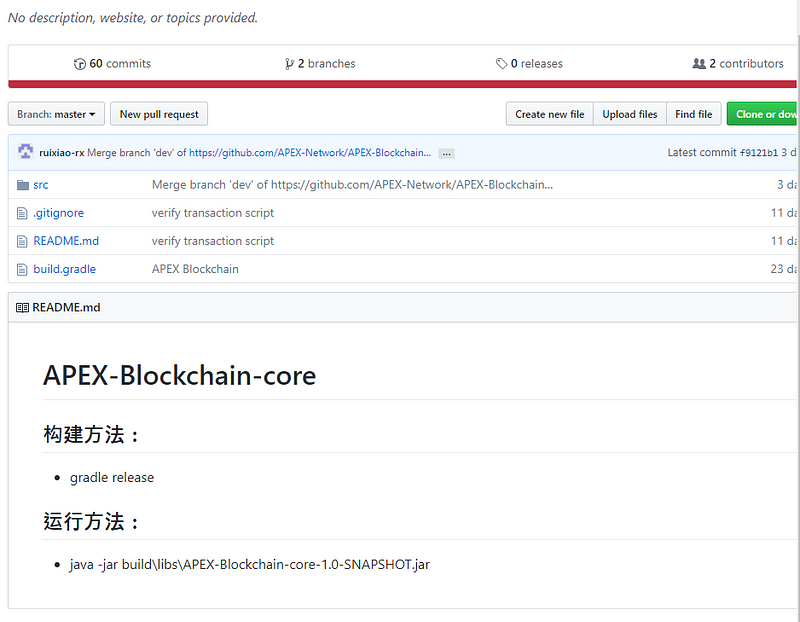
Grade, scala, 2 contributors, 60 commit, aboriginal accomplish 23 canicule ago
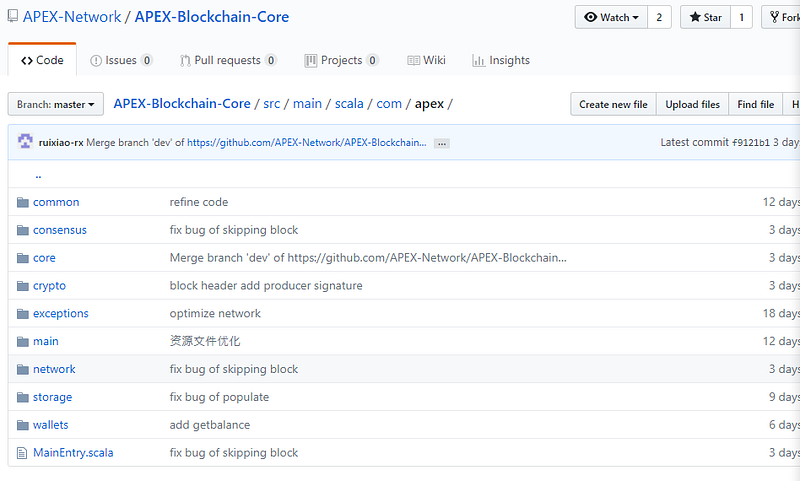
All the accepted suspects.
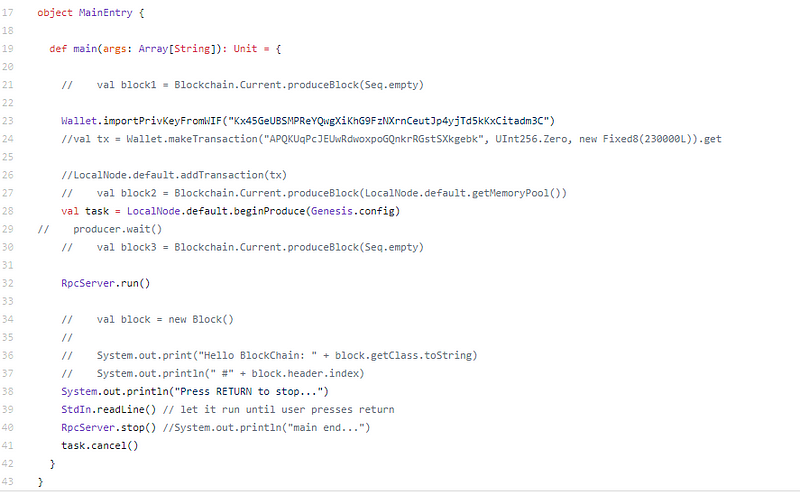
Main mostly acclimated for testing, WIF hardcoded. Not a abundant start.
This cipher was started about the 27th July. Apex listed in April. Guess it took them 4 months to acquisition developers.
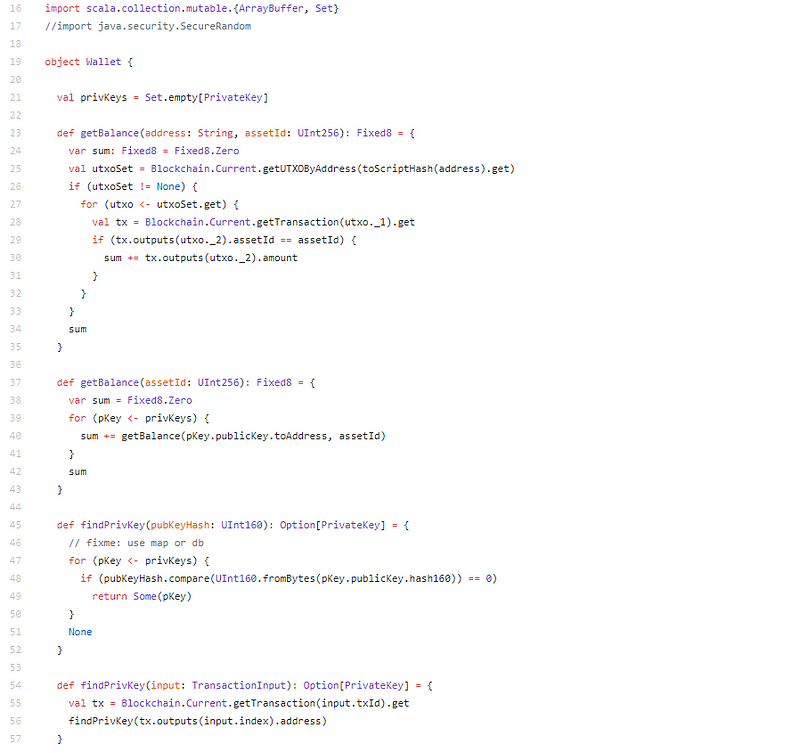
UTXO, script, WIF. Is this aloof bitcoin accounting in Scala?
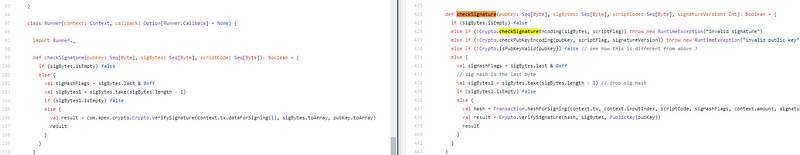
Left, Apex Script, appropriate bitcoin-lib script. Exactly the aforementioned except for some absurdity administration that was removed in the Apex version.
More affected code.
This is “consensus”. Nothing here, affective on.
The blow is boiler plate. There is annihilation here.
Apex Network Code Review Conclusion:
I can’t even.
You can babble about Apex Network in our Telegram group.
Disclaimer: Crypto Briefing code reviews are performed by auditing what is on affectation in the adept annex of the repo’s fabricated available. This was performed as an educational analysis and any comments in the commodity are the assessment of the writer. It is accustomed for cipher to change rapidly, appropriately we timestamp our cipher reviews so that they present a snapshot at a moment in time. Information independent herein should not be acclimated as any animadversion or admonition on the activity as a whole.
Apex Network Code Review Timestamp: August 19th 2026














