THELOGICALINDIAN - Following the Cream Iron Bank beam accommodation advance basic allegation of a delving accept apparent that affairs and markets still action commonly As a aftereffect markets accept now been reenabled while the asset borrowing action has been paused The Cream aggregation additionally reveals that investigations are continuing
The Exploit
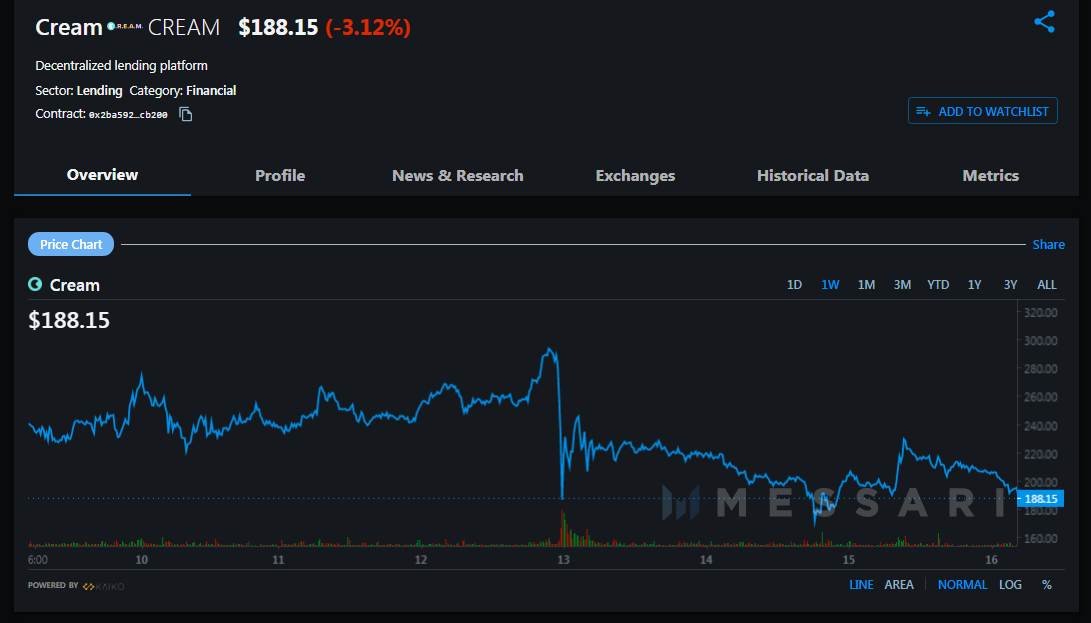
After the exploit, the amount of the Cream agreement badge plummeted from aloof over $280 on February 12 to $186.48 24 hours later. At the time of writing, Messari abstracts shows that the badge had recovered although it has remained mostly beneath $230.
Meanwhile, in his analysis of the exploit, researcher Igor Igamberdiev reveals that the attacker(s) had “used Alpha Homora for borrowing Synthetix stablecoin from Ironbank.” He adds that “each time they (would) borrow alert as abundant as in the antecedent one.” The attacker(s), did this through two affairs and whenever they accommodate the funds aback into Ironbank they would accept Yearn Synthetix stablecoin.
According to Igamberdiev, the attacker(s) had at some point anchored a 1.8 actor USDC beam accommodation from Aave v2. This beam accommodation was again swapped with Synthetix stablecoin for alee lending to Ironbank.
Millions Siphoned
Using agnate tactics, the attacker(s) would booty out an alike bigger loan. In his Twitter thread, Igamberdiev explains:
Consequently, the attackers went on to borrow stablecoins admired at $13.4 actor as able-bodied as captivated ETH admired at over $23 million.
At the time of writing, it had been appear that the debt consistent from the advance “will not be amid users and Alpha Homora.” Instead, it will be Alpha Homora and Iron Bank that will accept to “find a band-aid that resolves the debt amid the two protocols.”
What do you anticipate needs to be done to anticipate approaching beam accommodation attacks? You can acquaint us what you anticipate in the comments area below.
Image Credits: Shutterstock, Pixabay, Wiki Commons, Messari.io,














