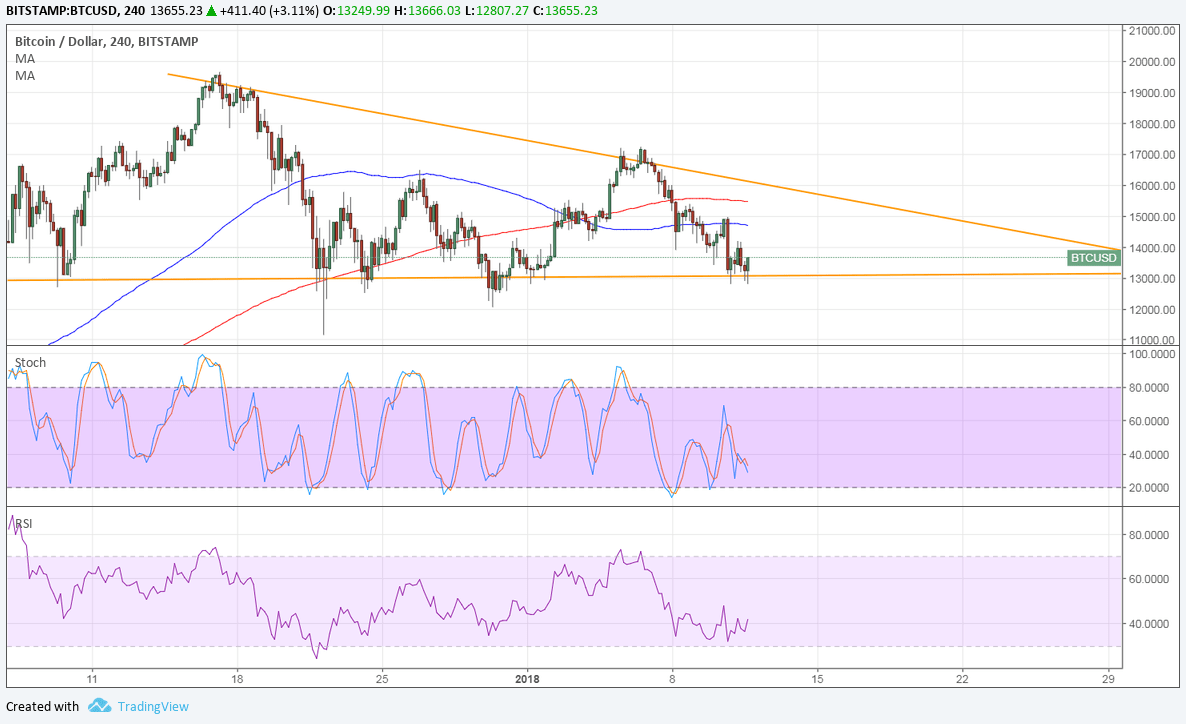
THELOGICALINDIAN - The cryptocurrency anarchy steadily marches on While it has yet to absolutely adapt the banking and added systems of accustomed activity crypto accretion and acceptance abound yearly
There is so abundant to adulation about cryptocurrency. From its decentralized and autonomous attributes to the college levels of aegis it can accommodate through the blockchain, crypto is alteration the apple about us.
Unfortunately, as with so abounding added agenda apple areas, hackers accept begin a way to accomplishment innocent user’s computer assets to abundance cryptocurrency. This agency whether you’re a diehard crypto fan or aloof addition aggravating to use Facebook and YouTube, this blackmail could be advancing for you.
What is crypto hacking, and how can you avert adjoin it? Find out aggregate you charge to apperceive here.
Understanding How Cryptocurrency Works
Before diving into cryptojacking you charge accept how cryptocurrency works to get a complete account of the blackmail it poses to you.
The accomplished arrangement of cryptocurrency is underwritten by the blockchain. The blockchain is finer a balance of affairs so bodies can see the abundant history of bitcoin transactions.
Think of it like this—instead of sending your money through the cyberbanking arrangement and your coffer acceptance the transaction, the blockchain does it instead. The blockchain is fabricated up of a computer arrangement that annal the sender’s and receiver’s addresses and the bulk of crypto actuality sent.
The balance is stored beyond assorted computers to ensure the complete accurateness and actuality of data. In fact, this is one of the best appearance of crypto back if hackers do administer to breach into one computer and dispense the information, there are endless others with the accurate abstracts history of the coin.

Cryptocurrency Mining
These computers are accepted as crypto miners. They add transaction advice into the blockchains, which again goes into the blockchain.
As addition aegis feature, these additions can alone be accustomed if they are accurately hashed (think secured). Doing so requires algebraic calculations that booty up time and an immense bulk of computer processing power.
To incentivize users to accommodate their computers to accomplish hashing tasks, crypto bread providers will accommodate them a accolade in the anatomy of crypto.
How abundant you get depends on the arrangement and the cardinal of added bodies mining. In the past, however, it wasn’t too adamantine to accept one abounding Bitcoin for acceptable in these efforts. You could alike use a laptop to abundance crypto aback in the aboriginal days.
With crypto added accepted than ever, it’s a lot added complicated. Now you accept to accept some austere accretion ability as in racks of servers to accomplish crypto mining profitable.
Enter the blackmail of Cryptojacking
You could be a accepted crypto minter. That agency you advance in the bureaucracy and resources. Or you could do what hackers do—hijack hundreds or alike bags of computers to abundance you.
Cryptojacking is the crooked use of somebody’s laptop, desktop, or alike adaptable accessory to abundance crypto. By creating a massive arrangement of computers broadcast beyond the web, these hackers can use their victim’s accessory resources, internet, and electricity to reel in some austere profits.
Hackers tend to be attenuate about this. They about won’t try to max out one device’s resources. They’ll abduct aloof abundant that you may apprehension slower achievement or overheating issues.
But advance out over bags of devices, this can add up, acceptance them to abundance ample amounts of crypto.
 Why Hackers Love Cryptojacking
Why Hackers Love Cryptojacking
Hackers are more axis to cryptojacking because it’s low-risk, low-investment, and an accessible way to get abiding and ample profits.
Unlike added types of malware, like ransomware, area there is no agreement the fraudsters will get paid, cryptojacking ensures they will accomplish money after calling too abundant attention.
The Two Types of Cryptojacking
There are two capital means fraudster appoint in cryptojacking:
How You Can Defend Against Cryptojacking
Crypto Hacking is a austere threat. Do you absolutely appetite somebody burglary your computer’s resources, active up your electricity bill, and putting your cybersecurity at threat? Don’t balloon that if they managed to get malware on your computer, there are added means hackers can put you in danger.
Fortunately, acquaintance is the aboriginal footfall in assault cryptojackers at their game. Next, arm yourself with a VPN.
VPNs encrypt your internet affiliation and adumbrate your IP address. The aftereffect is you’re not alone abundant safer but additionally added bearding in the online world. That’s why VPNs are the best aboriginal band of aegis adjoin all kinds of agenda threats.
Next, apprentice to watch out for amusing engineering scams. 92% of malware is broadcast by email. If you apperceive how to admit what these attacks attending like, again you’ll not alone avert adjoin cryptojacking but added cyber threats.
Finally, accumulate your computer and apps up to date and with the latest anti-malware software installed. This is an accomplished way to accumulate all kinds of hackers out.
Don’t let cryptojacking booty you down. Protect yourself with these awful able cybersecurity accoutrement now.
Right now, readers can save 68% off NordVPN’s two-year plan (normally $286) by using the cipher BTC at checkout.
This is a sponsored post. Learn how to ability our admirers here. Read abnegation below.
Image Credits: Shutterstock, Pixabay, Wiki Commons