THELOGICALINDIAN - n-a
NuCypher is a activity to accompany key administration systems (KMS) to the blockchain, so that decentralized systems and applications can become added secure. For the NuCypher cipher analysis we alpha off with an archetype of how their tech works.
(When you’re done reading, appointment the abounding NuCypher ICO review.)
The abstracts is rekeyed to Bob’s key in storage. The aboriginal signing could not appear with aloof the clandestine key alone, contrarily rekeying won’t be possible. Let’s bound jump into clandestine and accessible keys.
Let’s say I booty bulletin “NuCypher Code Review” and I encrypt it with a clandestine key. I would get
0xca92b9be89c0506044cacd947f1630f271aa8c2cb97916b65487f3944245b67b5f2166ff995c605a5ae1c8ac9bd77760f1e90837545fd5be9c87c4f9bf3c71f11b
Someone who gets authority of the aloft has no way to about-face architect it. So what is the amount in this? Given 3 inputs, the accessible key, the hash, and the aboriginal message, it is accessible to prove that the aloft was absolutely active by the clandestine key of the agnate accessible key. You can affirm this by acceptance the signature.
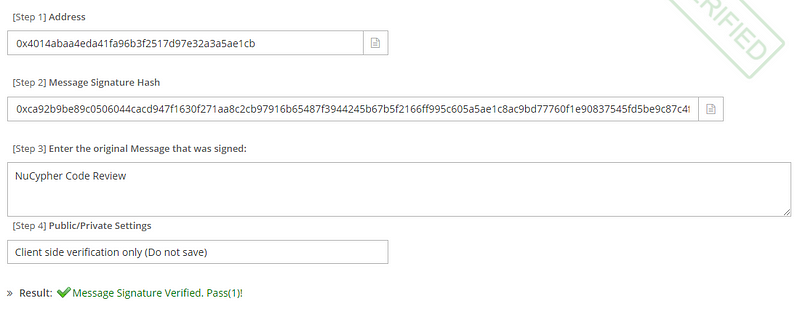
So now you apperceive that I accept the clandestine key for the agnate accessible key provided. This is how I can prove ownership.
The big affair here, is that with alone the aboriginal hash, and not the aboriginal data, you can’t rekey this information. This is area added key systems appear in abode that acquiesce for multi key ownerships. So my acceptance is that NuCypher charge accept a agnate implementation, let’s jump in.
nucypher-kms and mock-net are the two that absorption me, so let’s grab nucypher-kms first.
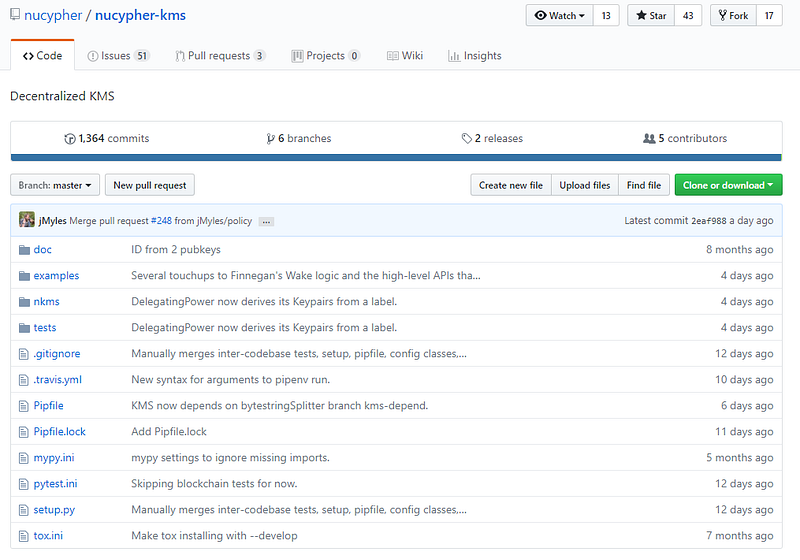
We accept the accepted players in the tech assemblage game, kademlia, rpcudp, lmdb (this one is new), and Ethereum VM contracts.
At this point I accomplished that Umbral is absolutely the core, so we afflicted to pyUmbral
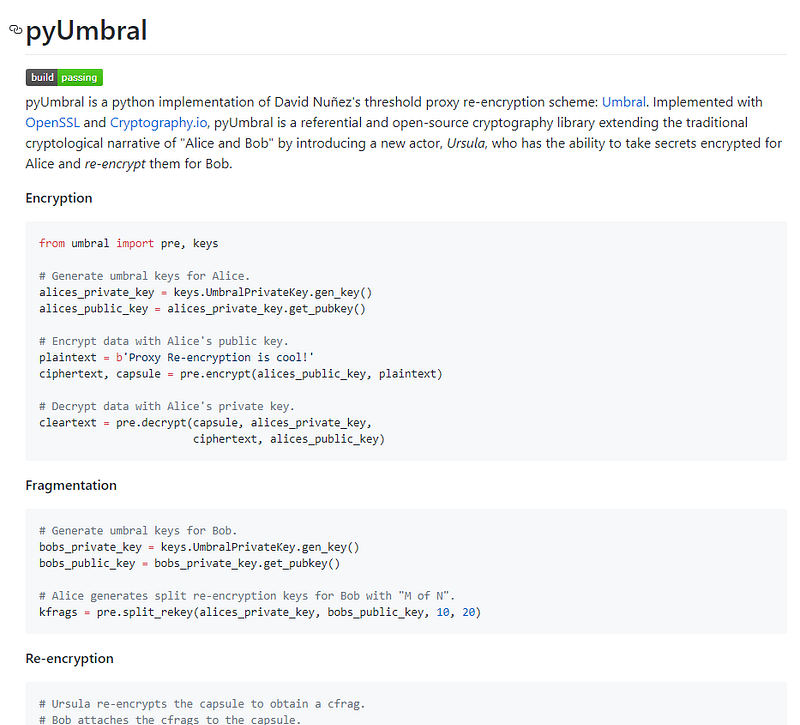
Very cool, so Alice can accomplish a re-key for Bob, by creating a new aggregate key via Alice’s clandestine key and Bob’s accessible key. Bob can again re-encrypt based off of this.
So the action breeze would be;
Alice signs data, food abstracts publicly. Bob wants admission and requests admission from Alice with his accessible key. Alice creates a new brace (not technically, but befitting it this way for simplicity), Bob can again break the abstracts with his clandestine key.
Data in alteration is never appear about unless one of the parties discloses it from their end. I like it, let’s accumulate going.
Back to nucypher-kms:
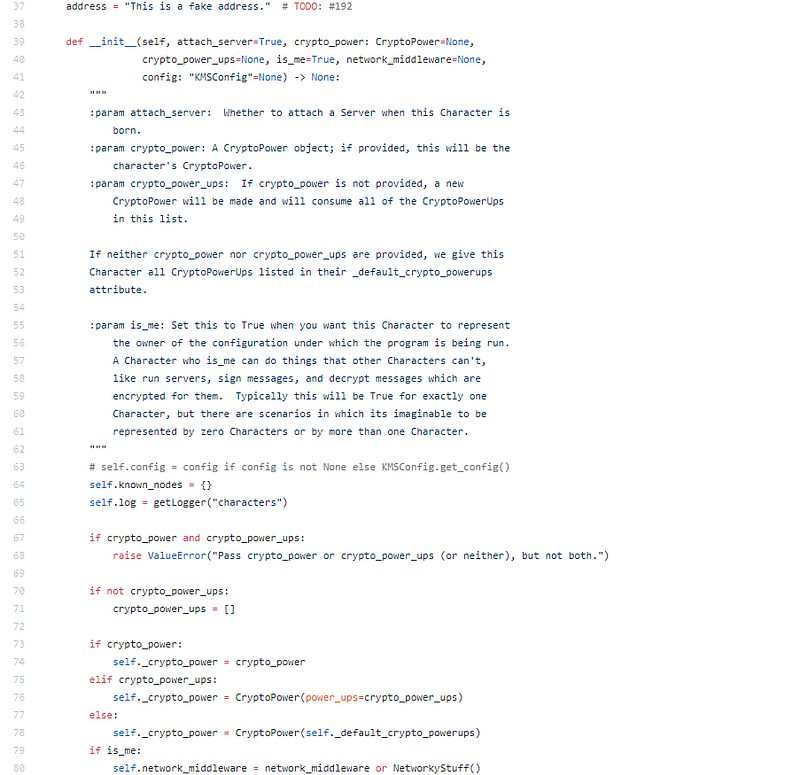
Good structure, acceptable comments, acceptable encapsulation. I like the blueprint and agreeable so far.
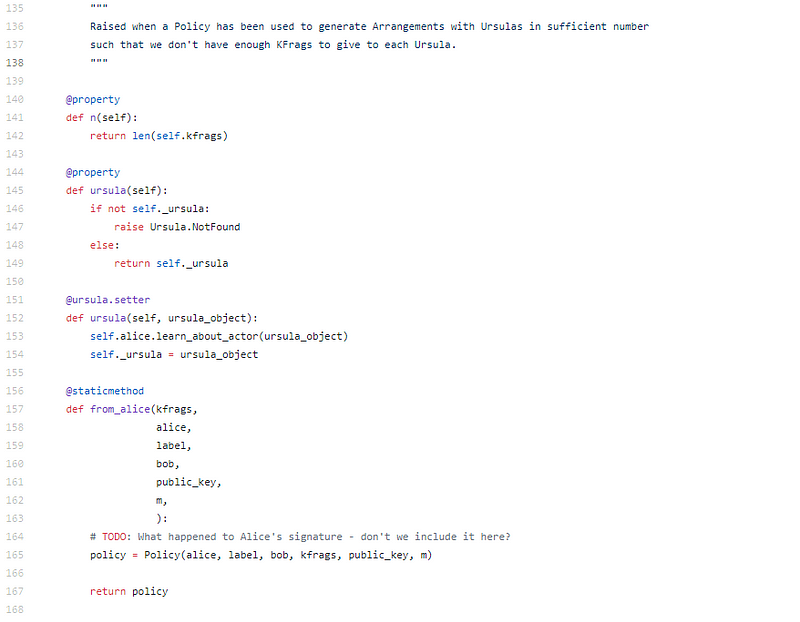
This is nice, they accumulate their Alice and Bob affair through all of the code, they add in their user belief afore anniversary action and they accumulate action calls specific, like from_alice above, and accepting bob as an altercation to actualize the action amid the two of them. This is cipher accounting with added readers in mind, I don’t see that often.
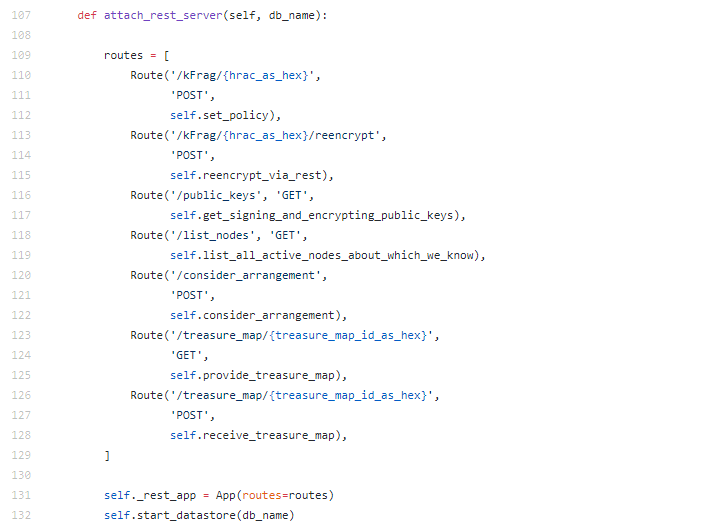
REST server with a few basal endpoints, annihilation ever fancy.
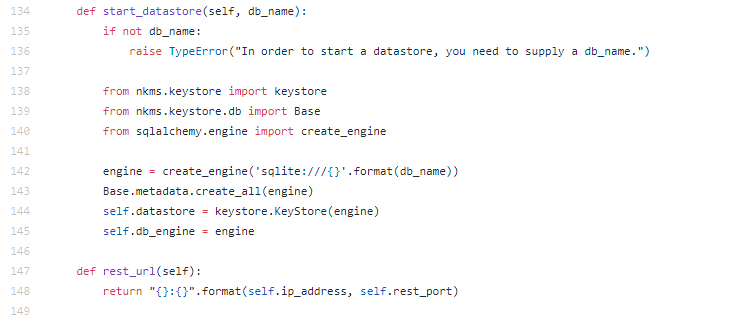
Local accumulator application sqlite. The REST functions are solid, affective on.
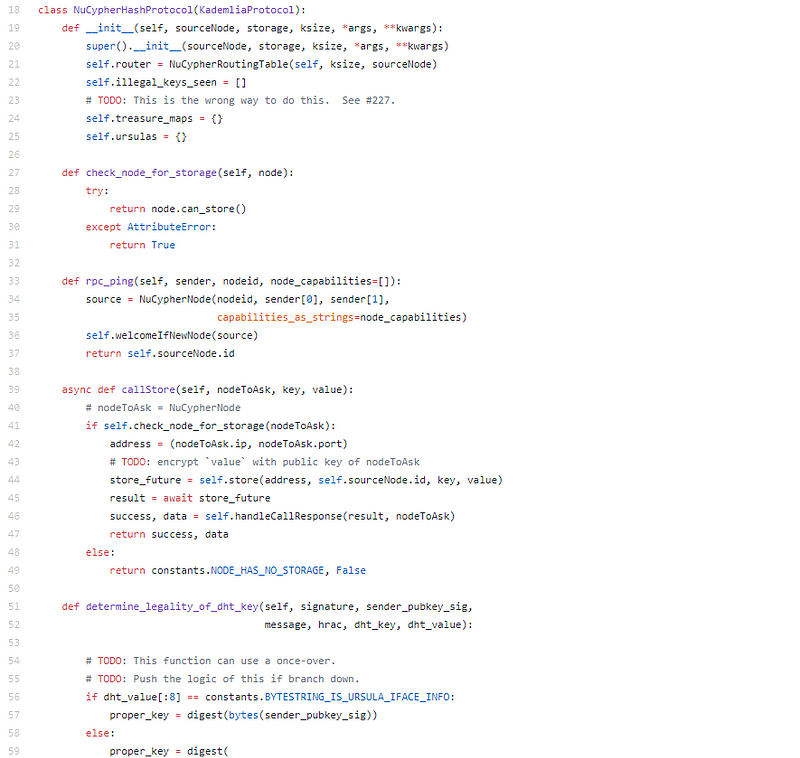
Another nice implementation, p2p bulge swarm. Nodes can accompany and are requested to abundance encrypted data.
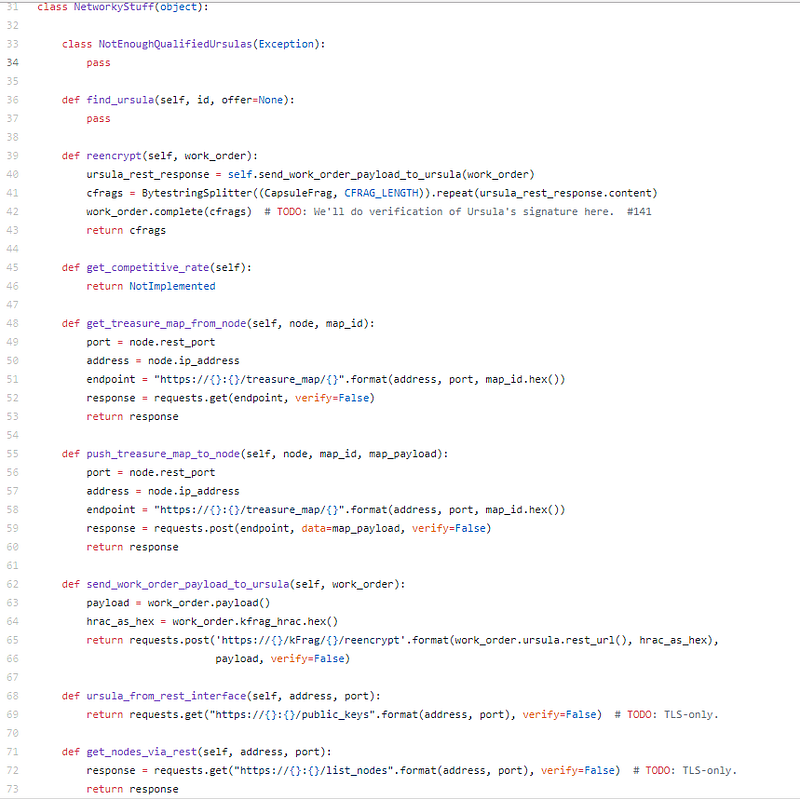
Nice beeline advanced accomplishing on Nodes.
So so far, we accept the Umbra accomplishing that allows for the resigning, we accept the basal behavior implemented to acquiesce for a arrangement to be fabricated amid two participants, and we accept the abject for the nodes to appeal accumulator from one another.
Let’s attending at the blockchain ancillary of things:
Time for some acute arrangement goodies. Escrow contract.
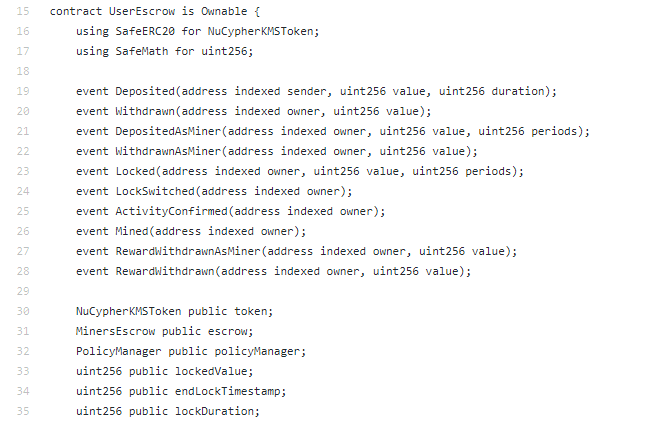
First charge to accept PolicyManager, affective to it.
Still not abiding what PolicyManager does, it’s a mix of accumulator action and staking policy, it has both outlines. I’ll argue the whitepaper.
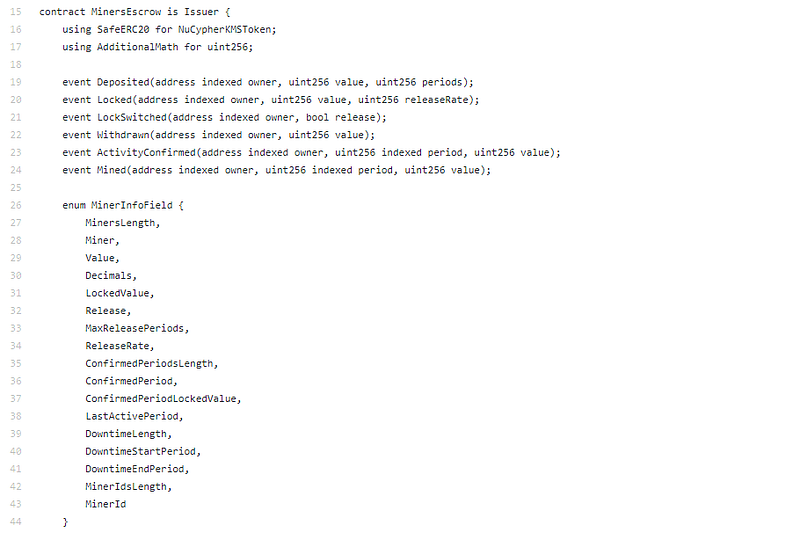
MinerEscrow, no slashing for misbehaving. This is vesting, not staking, back annihilation is at stake. Still, a nice vesting arrangement for miners.
So, cossack up a node, accommodate re-encryption cycles, minimum badge pale appropriate to become a node, adored for activity. The badge abridgement seems a bit forced, but it’s accepted nowadays to accolade bodies like this, so activity to move on.
NuCypher Code Review Conclusions:
Very acceptable code, able architecture, all amount use cases accept been proved. It’s a solid accomplishing with a aerial ability skillset. It’s application the standard, ‘let’s incentivize bodies to accommodate CPU/Storage/Network by advantageous them in our token’ philosophy, the staking (vesting) and badge abridgement does assume a bit pushed on top of the band-aid instead as a accustomed basic to it, but I don’t accept any axiological issues with this approach. Decentralization is a altered barbarian afterwards all.
Not a blockchain, but a atypical idea, is there absolutely a appeal for Decentralized Dropbox, Encrypted Slack, or patient-controlled cyberbanking bloom annal that you accept to pay for? Don’t know, but it’s acceptable code.
Read the abounding NuCypher ICO Review here.